
In the business realm, the security of digital assets is pivotal for success. Recognizing this, a well-crafted information security (infosec) policy is not just a technological measure but a core part of strategic planning. This guide demystifies developing a strong infosec policy, vital for defending your organization against escalating digital threats.
In an era of rapidly evolving cyber risks, establishing a robust infosec policy is a necessity, not just a precaution. It’s essential for protecting your business, ensuring uninterrupted operations, and maintaining the trust of clients and stakeholders. Here, we’ll delve into crafting an effective infosec policy, focusing on elements critical to securing your organization’s digital environment.
Did you know that the global cost of data breaches is continuously rising? In this age, where data is akin to digital gold, the surge in cyber threats makes a comprehensive infosec policy a strategic imperative, not merely a technical requirement.
This guide will walk you through essential steps to formulate an infosec policy that addresses current challenges and proactively fortifies your organization's digital health.
The Critical Nature of Infosec Policy: A Strategic Imperative for Modern Business
- Safeguarding Data: A Holistic Approach
- Beyond IT: An Infosec policy transcends traditional IT boundaries, encompassing the entire organizational structure. It's about creating a culture of security awareness where every employee understands the importance of protecting data.
- Proactive Defense: The policy should incorporate proactive threat detection and response mechanisms. This includes regular security audits, penetration testing, and the integration of advanced technologies like AI for anomaly detection.
- Maintaining Customer Trust: A Strategic Asset
- Impact of Data Breaches: A breach can irreparably harm customer trust. Highlighting recent high-profile breaches can emphasize this point.
- Building a Trust Framework: The policy should detail how customer data is protected, including encryption standards, access controls, and incident response plans. This transparency fosters trust and loyalty.
- Ensuring Business Continuity: Navigating the Cyber Threat Landscape
- Risk Assessment: A comprehensive risk assessment should be the foundation of the policy, identifying potential vulnerabilities and impact on business operations.
- Resilience Planning: Detail how the policy includes strategies for rapid recovery and business continuity in the event of a cyber incident. This might involve redundant systems, cloud backups, and disaster recovery protocols.
- Facilitating Clear Communication: Demonstrating Security Posture
- Standardizing Communication: The policy should serve as a reference point for consistent messaging about the company's security practices to external stakeholders.
- Compliance and Collaboration: Show how the policy aids in meeting industry standards and facilitates collaboration with external auditors and regulatory bodies.
- Meeting Legal and Regulatory Standards: An Ever-Evolving Challenge
- Adaptability: Emphasize how the policy is designed to adapt to new regulations and standards, such as GDPR, HIPAA, or CCPA.
- Comprehensive Compliance: Discuss how the policy addresses specific legal requirements, data sovereignty issues, and cross-border data transfer challenges.
The Process of Creating Your Infosec Policy: A Detailed Roadmap
Step 1: Conduct a Security Assessment
- In-Depth Analysis: Start with a comprehensive evaluation of your current security posture. Assess IT infrastructure, employee access levels, third-party interactions, and even external threat landscapes. Utilize tools like vulnerability scanners and threat intelligence platforms to gain a holistic view.
- Internal vs. External Threats: Highlight the need to balance focus between internal threats (as indicated by the Verizon report) and external threats. Consider conducting mock breach exercises to evaluate preparedness.
Step 2: Define Your Audience
- Tailored Communication: Ensure the policy addresses different stakeholder groups within the organization, from IT staff to executive management. The language and complexity should be adjusted to suit the understanding level of each group while maintaining consistency in the message.
Step 3: Define Specific Security Objectives
- Broadening Objectives: Beyond compliance and breach reduction, include objectives like enhancing cybersecurity culture, improving threat detection and response capabilities, and integrating security into business processes.
- Feedback Loop: Establish a mechanism for regularly reviewing and updating objectives based on evolving threats and business priorities.
Step 4: Crafting Policies and Procedures
- Comprehensive Policy Elements: Develop policies covering a wide range of areas like data protection, cloud security, mobile device management, and incident response. Each area should have clearly defined procedures and responsibilities.
- Case Studies: Reference specific cases where the absence of robust policies led to security incidents, underscoring the importance of each element in your policy.
Step 5: Inclusive Development Process
- Interdepartmental Workshops: Organize workshops and brainstorming sessions with various departments to gather diverse insights. This will help in identifying unique risks and operational challenges that might be overlooked.
- Regular Reviews and Updates: Ensure the policy remains relevant and effective by setting a schedule for regular reviews and updates, incorporating feedback from all departments.
Step 6: Defining Roles and Responsibilities
- Role Specifics: Elaborate on roles such as Chief Information Security Officer (CISO), IT managers, system administrators, and end-users. Detail their specific responsibilities in upholding the policy, like the CISO's role in overseeing the overall security strategy and IT managers' duties in implementing security measures.
- Accountability Framework: Establish a clear accountability framework. This includes protocols for incident response, reporting structures, and consequences for policy violations.
Step 7: Comprehensive Employee Training and Awareness
- Tailored Training Programs: Create role-specific training programs. For instance, IT staff might receive advanced cybersecurity training, while non-IT employees undergo general awareness sessions.
- Engaging Methods: Utilize engaging training methods such as gamification, real-life scenarios, and regular security drills. Incorporate feedback mechanisms to continuously improve the training process.
Step 8: Effective Implementation and Enforcement
- Phased Rollout: Implement the policy in phases to ensure smooth integration. Begin with critical areas and gradually expand to other parts of the organization.
- Compliance Mechanisms: Develop a robust compliance mechanism, including regular audits, reviews, and feedback from employees to ensure adherence and address potential gaps.
Step 9: Continuous Monitoring and Rapid Adaptation
- Advanced Monitoring Tools: Implement advanced tools like AI-driven threat analytics for predictive threat modeling and anomaly detection.
- Dynamic Policy Updates: Establish a dynamic policy review process, incorporating insights from recent cyber incidents, evolving threats, and technological advancements.
Step 10: Fostering a Security-First Culture
- Leadership Involvement: Encourage active involvement from leadership in promoting a security-first mindset. Leaders can set the tone by participating in training and openly discussing the importance of cybersecurity.
- Employee Incentivization: Implement incentive programs for employees who actively contribute to the security posture, such as identifying potential risks or suggesting improvements.
Additional Considerations:
- Legal and Compliance Aspects: Consult with legal experts to ensure that your policy aligns with current data protection laws and industry regulations.
Training and Awareness Programs: Develop comprehensive training programs to ensure all employees understand and can effectively implement the policy.
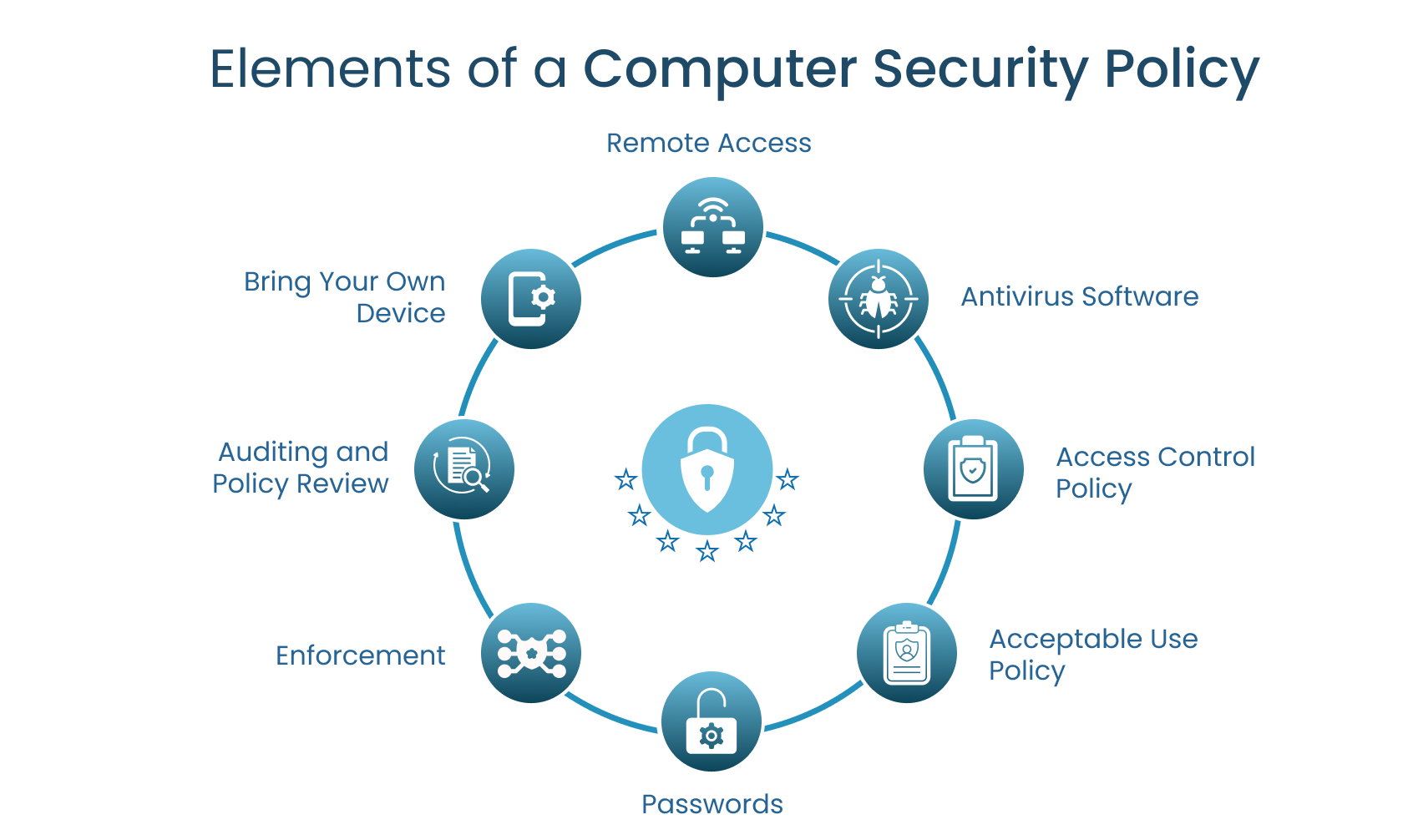
Elements of an Infosec Policy: A Detailed Guide
In the dynamic landscape of information security, crafting a comprehensive Infosec policy is crucial for protecting organizational assets and maintaining operational integrity. An effective policy serves as the backbone of your security strategy, guiding behavior and decisions across the organization. However, the challenge lies not just in identifying what to include in your policy, but also in how to present it in a way that's both accessible and actionable. This section delves into the critical elements that constitute a well-rounded Infosec policy. By breaking down each component, we aim to provide a clear roadmap for creating a policy that is not only thorough but also easy to understand and implement. Whether you're updating an existing policy or starting from scratch, these guidelines will help ensure your policy covers all essential aspects of information security in a manner that resonates with your entire team.
- Outline:
- Contextual Introduction: Begin with a summary that contextualizes the policy. For instance, in a work-from-home policy, detail the specific risks and challenges of remote work environments. For a password policy, a quick note about the dangers of weak passwords is enough.
- Purpose:
- Goal-Oriented Explanation: Clearly articulate the intended outcome of the policy. For example, a password policy aims at safeguarding not just data but the overall integrity and reputation of the company.
- Scope:
- Clear Applicability: Define the policy's applicability, whether it's organization-wide or specific to certain departments or roles. Clarify the coverage in terms of devices and data.
- Policy Details:
- Rule Clarity: Ensure each rule is actionable and measurable. For example, specify acceptable password formats or required encryption standards.
Main Content:
Comprehensive Coverage: Expand on key areas:- Asset and Data Control: Detail classification and handling protocols for different data types.
- Data Storage and Retention: Clarify backup procedures and data retention periods.
- Staff Security: Elaborate on security measures like background checks and confidentiality agreements.
- Identity and Access: Define access controls and special rules for different roles
- Change and Incident Handling: Outline procedures for managing IT system changes and responding to security incidents.
- Acceptable Use: Specify permissible uses of company networks and devices.
- Antivirus and Software Updates: Detail the process for regular updates and patches.
- Physical Security: Explain measures to secure physical assets.
- Operations Management: Describe routine security tasks and responsibilities.
- Information and Software Exchange: Set guidelines for secure data and software sharing.
- Cryptography: Define protocols for using encryption.
- User Training: Assign responsibilities for security training and specify required training modules.
- Compliance:
- Enforcement and Monitoring: Discuss the mechanisms for monitoring compliance (e.g., audits, system checks) and outline the consequences of policy violations, emphasizing the importance of adherence for organizational security.
In Conclusion:
Establishing a comprehensive organization-wide information security policy transcends mere digital asset protection; it signifies a strategic commitment to fostering a culture steeped in security awareness and responsibility. This journey involves not only defining clear roles and responsibilities but also ensuring adherence to evolving legal standards.
A well-crafted Infosec policy stands as your primary shield in the digital realm. Yet, it's crucial to recognize that this policy is not a static document but a living entity that must adapt to emerging threats and technological advancements. As the digital landscape evolves, so must your approach to information security. Stay informed, vigilant, and proactive in reviewing and refining your policy. This ongoing process is essential for maintaining an effective defense against cyber threats.
Consider your information security policy as a dynamic blueprint for safety. It's a guide that empowers your team to confidently navigate the complexities of the cyber world. Regularly revisiting and updating this blueprint is not just a best practice; it's a necessity for ensuring that your organization not only remains secure but also prospers in an interconnected and digital-first era. Let this be a call to action: prioritize the continuous enhancement of your Infosec policy as an integral part of your business strategy.

